In this post, we will explain how to enforce password policies in Linux, more specifically RHEL / Rocky Linux/ Alma Linux and Ubuntu / Debian. We will cover enforcing password policies such as password expiration period, password complexity and password length.
As much as Linux is considered a secure operating system, its security is just as good as the password strength of login users. Password policies exist to ensure that a strong password is set for users and as a Linux user, you should be mindful to enforce these policies to make it difficult for breaches to occur. You surely don’t want users configuring weak or guessable passwords which can be brute forced by hackers in a matter of seconds.
Enforce Password Policies in Ubuntu / Debian Linux
There are 2 main ways that you can enforce password policies. Let’s take a look at each in detail.
1) Configure the maximum number of days that a password can be used
For start, you can configure a password policy that requires users to change their passwords after a certain number of days. Best practice dictates that a password should be changed periodically to keep malicious users off-kilter and make it harder for them to breach your system. This applies not just in Linux but in other systems such as Windows and macOS.
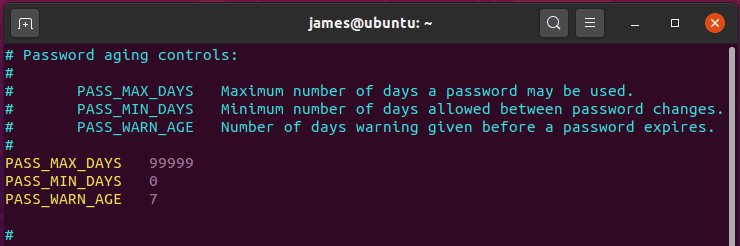
To achieve this In Debian/Ubuntu, you need to modify the /etc/login.defs file and be on the lookout for the PASS_MAX_DAYS attribute.
By default, this is set to 99,999 days as shown.
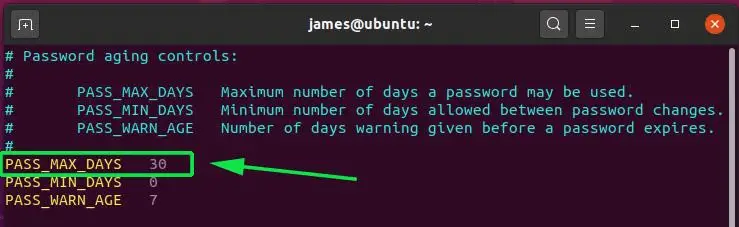
You can modify this to a reasonable duration, say, 30 days. Simply set the current value to 30 as shown and save the changes. Upon lapsing of the 30 days, you will be compelled to create another password.
2) Configure Password complexity with pam
Ensuring that password meets a certain degree of complexity is equally crucial and further thwarts any attempts by hackers to infiltrate your system using brute force.
As a general rule, a strong password should have a combination of Uppercase, lowercase, numeric and special characters and should be at least 12-15 characters long.
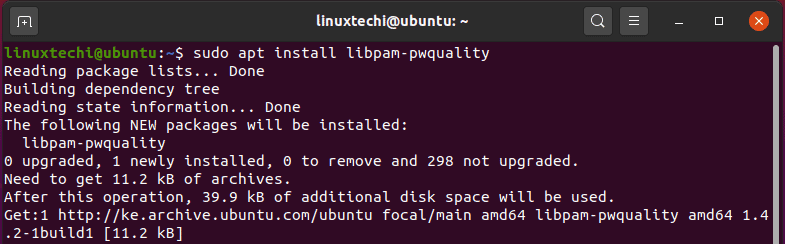
To enforce password complexity in Debian / Ubuntu systems, you need to install the libpam-pwquality package as shown:
$ sudo apt install libpam-pwquality
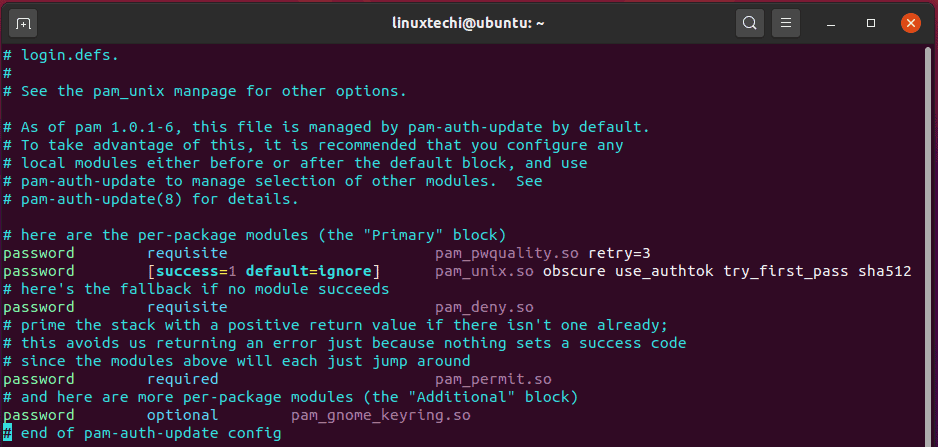
Once installed, head out to the /etc/pam.d/common-password file from where you are going to set the password policies. Be default, the file appears as shown:
Locate the line shown below
password requisite pam_pwquality.so retry=3
Add the following attributes to the line:
minlen=12 maxrepeat=3 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1 difok=4 reject_username enforce_for_root
The entire line should appear as shown:
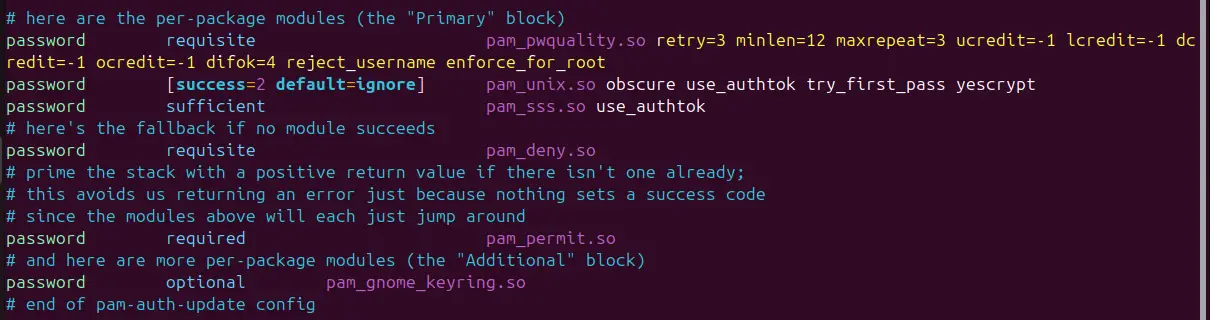
Let’s flesh out what these directives stand for:
- retry=3: This option will prompt the user 3 times before exiting and returning an error.
- minlen=12: This specifies that the password cannot be less than 12 characters.
- maxrepeat=3: This allows implies that only a maximum of 3 repeated characters can be included in the password.
- ucredit=-1: The option requires at least one uppercase character in the password.
- lcredit=-1: The option requires at least one lowercase character in the password.
- dcredit=-1: This implies that the password should have at last a numeric character.
- ocredit=-1: The option requires at least one special character included in the password.
- difok=3: This implies that only a maximum of 3 character changes in the new password should be present in the old password.
- reject_username: The option rejects a password if it consists of the username either in its normal way or in reverse.
- enforce_for_root: This ensures that the password policies are adhered to even if it’s the root user configuring the passwords.
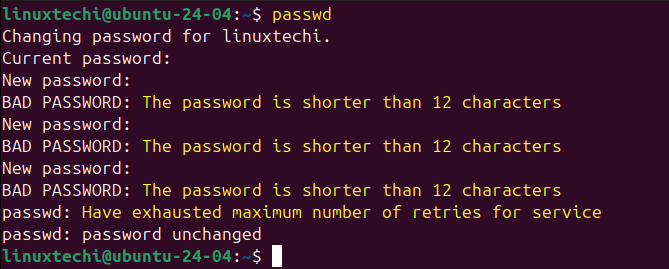
Now, try to test these password policies by setting up a weak password to your local user, you should get the error shown below:
Enforce Password Policies in RHEL / Rocky Linux / Alma Linux
For Debian and Ubuntu systems, we enforced the password policy by making changes to the /etc/pam.d/common-password configuration file.
For RHEL and other derivatives like Rocky Linux, Alma Linux and Fedora, we are going to modify the /etc/pam.d/system-auth or /etc/security/pwquality.conf configuration file.
So, proceed and open the file:
$ sudo vim /etc/pam.d/system-auth
Locate the line shown below
password requisite pam_pwquality.so try_first_pass local_users_only retry=3 authtok_type=
Append the options in the line as shown.
minlen=12 lcredit=-1 ucredit=-1 dcredit=-1 ocredit=-1 enforce_for_root
You will end up having the line below:
password requisite pam_pwquality.so try_first_pass local_users_only retry=3 authtok_type= minlen=12 lcredit=-1 ucredit=-1 dcredit=-1 ocredit=-1 enforce_for_root
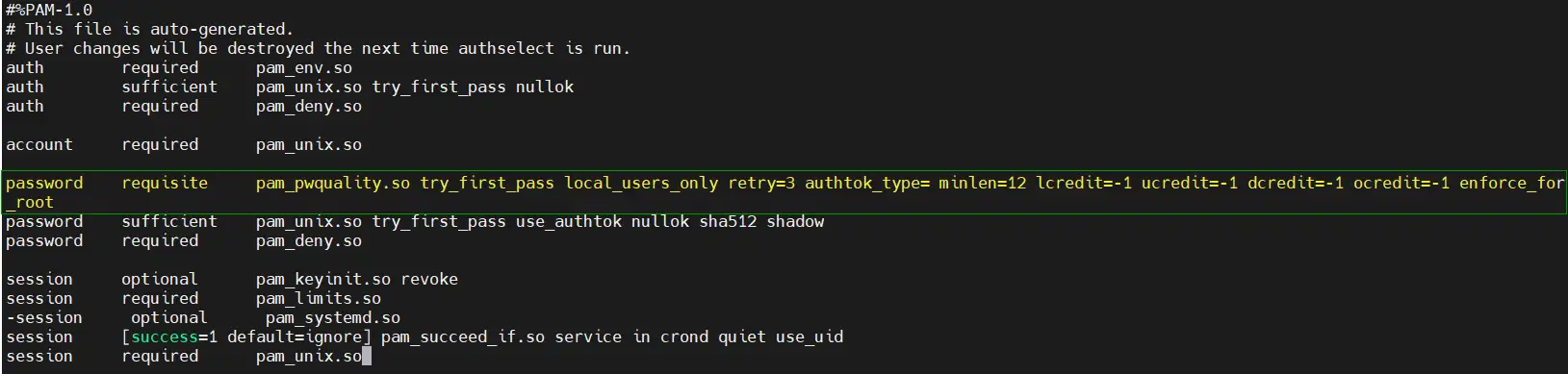
Once done, save the password policies and exit the file.
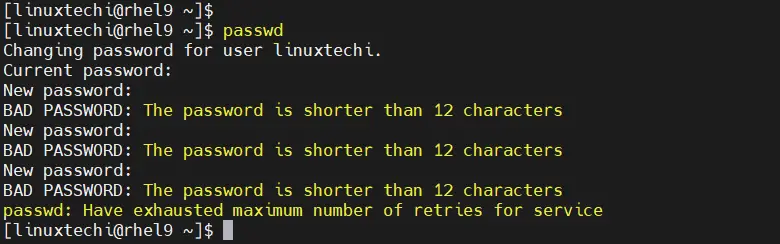
Once again, when you try creating a user with a weak password that doesn’t adhere to the enforced policies, you will encounter the error shown in the terminal.
Conclusion
As you have seen, enforcing a password policy is quite easy and serves as a superb way of preventing users from setting up weak passwords which may easy to guess or prone to brute-force attacks. By enforcing these policies, you can rest assured that you have fortified your system’s security and made it more difficult for hackers to compromise your system.
Read Also: How to Setup Passwordless SSH Login in Linux with Keys


I’ve enforced the above policy which is working fine for me. What if we need to expires hundred users to reset their passwords on next login? Because passwd -e user.name command will expire one user and for this command we need to provide a password to user so he can use this temp password to reset his / her new password at their first login.
Please assist, thanks in advance.
Hi FAHAD,
Create a small script and use for loop in the script to run ‘passwd -e‘ for hundred users.
Thanks Pradeep