Setting up passwordless SSH login in Linux enhances security and simplifies the process of logging into remote servers. By using SSH keys, you can log in to your Linux servers without entering a password, making automation and remote management easier.
This post will walk you through the steps to set up passwordless SSH login in Linux
Lab
- Jump Host (Rocky Linux) — SSH Client — 192.168.1.135
- Remote Linux System (Ubuntu 20.04) — 192.168.1.130
Let’s deep dive into the steps.
1) Generate an SSH Key Pair
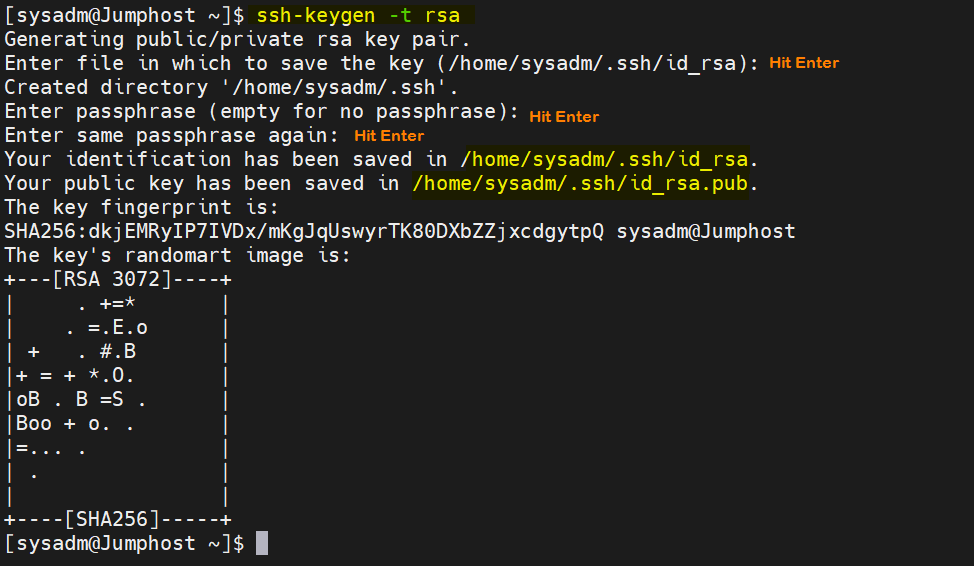
Login to jump host, in my case I am using ‘sysadm’. Run ssh-keyen command to generate Public and Private keys for sysadm using rsa algorithm
$ ssh-keygen -t rsa
This command will prompt you to enter path of public and private keys, if you want to keep the default path then hit enter and also hit enter when prompting to set the passphrase.
Output of ssh-keygen command would look like below,
Note: By default, ssh-keygen command generate keys of size 2048 bits. If you wish to change the size of keys, then use ‘-b’ option followed by size in bits. Example is shown below,
$ ssh-keygen -t rsa -b 4096
2) Copy Public Key to the Remote Server
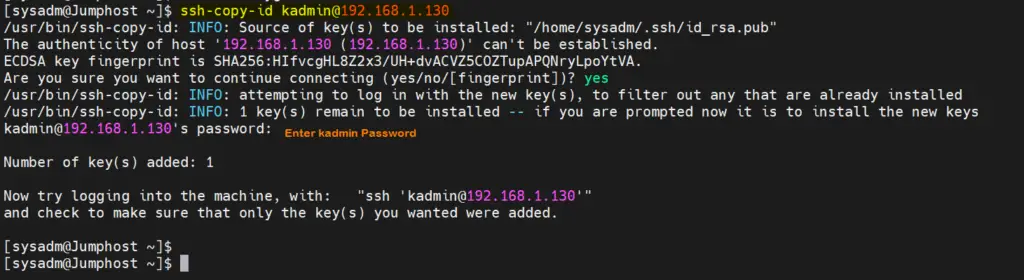
Now that you have generated the SSH keys, you need to copy the public key to the remote server where you want to set up passwordless SSH login. Use ‘ssh-copy-id‘ command to copy user’s public key to remote system.
Syntax:
$ ssh-copy-id <user-name>@<Remote-Linux-System-IP>
$ ssh-copy-id [email protected]
You will be prompted to enter the password for the remote user. Once entered, the public key will be copied to the remote server.
Output
3) Test Passwordless SSH Login
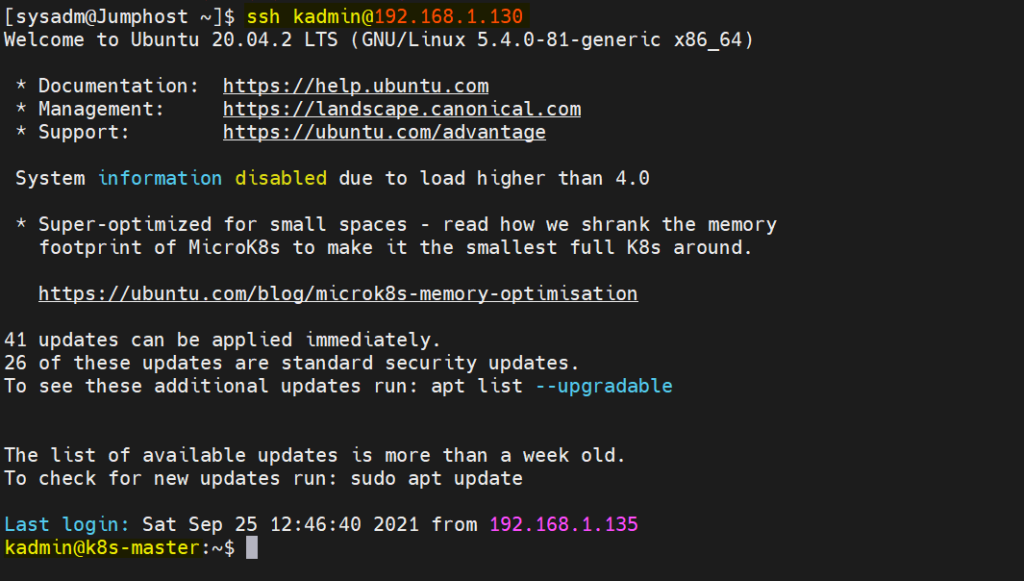
Now try to ssh remote system from jump host.
$ ssh [email protected]
Output,
Perfect, above output confirms that we can login to remote system without specifying any password.
Following are the important points to be considered while setting up passwordless authentication.
- Once the keys are exchanged and tested then we should disable root login and password based authentication for root and other users.
To achieve this, edit the ‘/etc/ssh/sshd_config’ file and set the following parameters.
PermitRootLogin no PubkeyAuthentication yes PasswordAuthentication no UsePAM yes
Save and exit the file and the restart the ssh service using below systemctl command.
$ sudo systemctl restart sshd
- Another important point is that remote user, in our case ‘kadmin’ should be part of sudo group and have admin rights so that it can perform administrative tasks.
That’s all from this post, I hope you have found it useful and informative, Please do post your queries and feedback in below comments section.
Also Read: 10 iftop Command Examples in Linux