In Most of the Organizations users and groups are created and managed on Windows Active Directory. We can integrate our RHEL 7 and CentOS 7 servers with AD(Active Directory) for authenticate purpose. In other words we can join our CentOS 7 and RHEL 7 Server on Windows Domain so that system admins can login to these Linux servers with AD credentials. While creating UNIX users on AD we can map these users to a specific group so that level of access is controlled centrally from AD.
In this article we discuss how to integrate CentOS 7.x & RHEL 7.x with AD(Windows Server 2008 R2 & Windows Server 2012 R2). Following steps are applicable for both CentOS 7 and RHEL 7.
Step:1 Install the required packages using yum command
Use the yum command to install following packages from the command line.
[root@servera ~]# yum install sssd realmd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools krb5-workstation openldap-clients policycoreutils-python
Update the /etc/hosts file and /etc/resolv.conf so that dns name or hostname of AD server gets resolved correctly. In my case AD server hostname is “adserver.example.com“, so place the below line in /etc/hosts file
192.168.0.151 adserver.example.com adserver
Contents of resolv.conf should be something like below. Just replace the domain name and ip address of dns server as per your setup
[root@servera ~]# cat /etc/resolv.conf search example.com nameserver 192.168.0.151 [root@servera ~]#
Step:2 Now Join Windows Domain or Integrate with AD using realm command
When we install above required packages then realm command will be available. We will use beneath realm command to integrate CentOS 7 or RHEL 7 with AD via the user “tech”. tech is a bind user which have required privileges on AD or we can also administrator user of AD Server for integration purpose.
[root@servera ~]# realm join --user=tech adserver.example.com Password for tech: [root@servera ~]#
Now verify whether our server has joined the Windows domain or not. Simply run the command ‘realm list‘
[root@servera ~]# realm list example.com type: kerberos realm-name: EXAMPLE.COM domain-name: example.com configured: kerberos-member server-software: active-directory client-software: sssd required-package: oddjob required-package: oddjob-mkhomedir required-package: sssd required-package: adcli required-package: samba-common-tools login-formats: %U@example.com login-policy: allow-realm-logins [root@servera ~]#
Whenever we run ‘realm join’ command it will automatically configure ‘/etc/sssd/sssd.conf‘ file.
Step:3 Check and Verify AD users on REHL 7 or CentOS 7 Servers
With ‘id‘ command on Linux we can verify the user’s uid and gid and their group information. At this point of time our server is now the part of windows domain. Use below command to verify AD users details.
[root@servera ~]# id linuxtechi@example.com uid=1997801106(linuxtechi@example.com) gid=1997800513(domain users@example.com) groups=1997800513(domain users@example.com) [root@servera ~]#
You might have noticed in above command that i have mentioned domain name as well along with user name because this is controlled by ‘/etc/sssd/sssd.conf’ file. If we execute id command without domain name then we will not get any details for user.
[root@servera ~]# id linuxtechi id: linuxtechi: no such user [root@servera ~]#
We can change this behavior by editing the file /etc/sssd/sssd.conf.
Change the following parameters from
use_fully_qualified_names = True fallback_homedir = /home/%u@%d
to
use_fully_qualified_names = False fallback_homedir = /home/%u
Restart the sssd service using following systemctl command
[root@servera ~]# systemctl restart sssd [root@servera ~]# systemctl daemon-reload
Now run the id command and see whether you are able get AD user details without mentioning domain name
[root@servera ~]# id linuxtechi uid=1997801106(linuxtechi) gid=1997800513(domain users) groups=1997800513(domain users) [root@servera ~]#
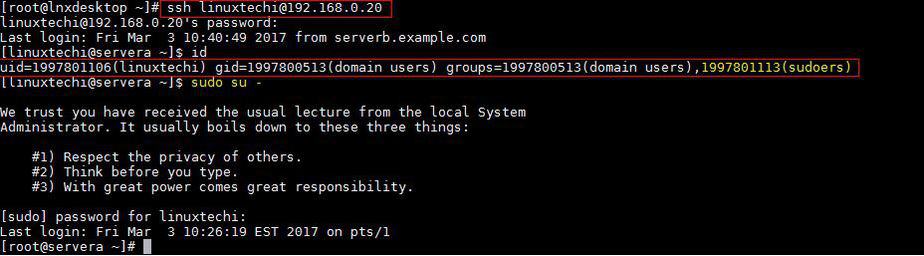
Let’s try ssh CentOS 7 or RHEL 7 Server with AD credentials
[root@lnxdesktop ~]# ssh linuxtechi@192.168.0.20 linuxtechi@192.168.0.20's password: Last login: Fri Mar 3 10:18:41 2017 from serverb.example.com [linuxtechi@servera ~]$ id uid=1997801106(linuxtechi) gid=1997800513(domain users) groups=1997800513(domain users) [linuxtechi@servera ~]$ pwd /home/linuxtechi [linuxtechi@servera ~]$
Step:4 Sudo rights for AD users on CentOS 7 or RHEL 7
In case you want to configure sudo rights for AD users then the best way is to create a group on AD with name sudoers and add Linux/UNIX users in that group and on Linux Server create a file with name “sudoers” under the folder /etc/sudoers.d/
Put the following content in the file.
[root@servera ~]# cat /etc/sudoers.d/sudoers %sudoers ALL=(ALL) ALL [root@servera ~]#
In my case I have given all the rights to the users which are part of sudoers group. Once your done with these changes re-login to your server with AD credentials and see whether user is part of sudoers group.
That’s all from this article, Hope you guys got an idea how to join RHEL or CentOS server with Windows Domain. Please share your feedback and valuable comments.



id: user@mydomain: no such user
my centos joined to AD .
Some lines of realm list are …..
configured: kerberos-member
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
login-formats: %U
login-policy: allow-realm-logins
But I couldn’t verify ad user on centos.
If you don’t mind, please help to me to solve it.
Hi Wai Htut Paing, looking at your output i can see that the login format is listed as %U which means it isn’t looking for the %D (Domain name)
so it seems you have already specified the login format or the system did this for you.
Hello Pradeep,
After executing realm list command when I am trying to execute the command id username@domain, It is giving me an error, realm : no such user found.
Kindly help me to resolve this issue
same issue facing
Hello Pradeep.
We recently integrated AD to centos 7.x . Users can login but after login it says /home/user/.bash_profile: permission denied.
Please advise
If the Active Directory is OFFLINE, will the users still be able to connect to the Linux servers using the account that is provided by AD?
Yes, User can login to their systems via AD credentials only if credentials are cached
I ran your above commands to join to the domain and I can query ID and realm list. But, I cannot log into the RHEL 7 server via SSH. Did I miss something?
A great post, thank you very much. To add, it would be nice to configure the NTP client. The idea is that the NTP client synchronizes time with the domain controller (DC). Here is an interesting guide to check: ‘https://www.sysadmit.com/2019/11/linux-anadir-equipo-al-dominio-windows.html’
Thanks Linuxtechi,
I followed the provided steps and it worked for me.
Now I have a different requirement or question.
1) I want to allow Only IT_TEAM OU. (Another OU should not log in)
2) Only Few users can have access from the allowed OU.
Hi,
We recently configured our system using the tutorial. However whenever a user logins, we get a message that .bash_profile cannot be created due to permission restriction. Our home directory is located on a lustre file system. Could that be a reason why permission is not given to users? Please advice
can someone tell me, is there a way to provide the password as an argument in the realm join command ? Just like
realm join -U -P example.com
I am trying to automate few areas where this password is actually occurring during the execution time so unable to supply this password as an argument
I joined the ad using the realm join –user=Administrator mydomain.com
however when i query id Administrator, the output is id: ‘administrator@mydomain’: no such user
Please let me know how to troubleshoot/debug the issue.
realm list contents are below:
type: kerberos
realm-name: MYDOMAIN.COM
domain-name: mydomain.com
configured: kerberos-member
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
login-formats: %U@mydomain.com
login-policy: allow-realm-logins