In this guide, we will learn how to sandbox Linux apps with Firejail and Bubblewrap.
Imagine you download a seemingly harmless PDF reader from the internet. You install it, open a file, and suddenly, without warning, your webcam light goes on. The browser logs out. Your SSH key is gone. By the time you realize something is wrong, it’s too late.
Linux is secure, but a single misstep can put your entire system at risk.
Every app you run has potential access to your entire digital life, including your files, credentials, network, and everything. And most apps don’t need that kind of freedom.
That’s where sandboxing tools like Bubblewrap and Firejail come in. They let you run risky or untrusted applications in isolated environments, limiting what they can see or do on your system. It’s like giving a stranger a room to stay in, but locking every door except the one they actually need.
Getting started with FireJail
Firejail is a Linux security tool that lets you sandbox applications and processes to reduce the risk of security breaches. It is lightweight and easy to use, and requires no in-depth system modifications or root-level setup.
Firejail uses Linux namespaces, seccomp filters, and AppArmor/SELinux (if available) to limit what a program can access, such as file system, network, or device files. This is like placing the application in a highly controlled environment where it only gets the minimum information it needs to run.
Installation of firejail
sudo apt install firejail -y
Key Features of firejail
- Internet access can be blocked (–net=none)
- Comes with a set of application profiles
- Can be run with custom profiles for strict access control
- Supports whitelisting folders or files
Sandbox Linux Apps with Firejail
Test a suspicious binary: You want to test a binary, but you don’t know if it’s safe. It could be a legitimate utility, or it could be malware designed to steal files, spy on you, or open a backdoor.
With this command, firejail (–profile) creates a temporary fake home directory and (–net=none) restricts the internet connectivity to the application.
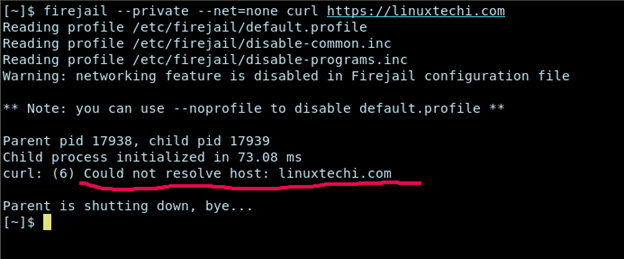
firejail --private --net=none ./maybe_malicious_binary firejail --private --net=none curl https://linuxtechi.com
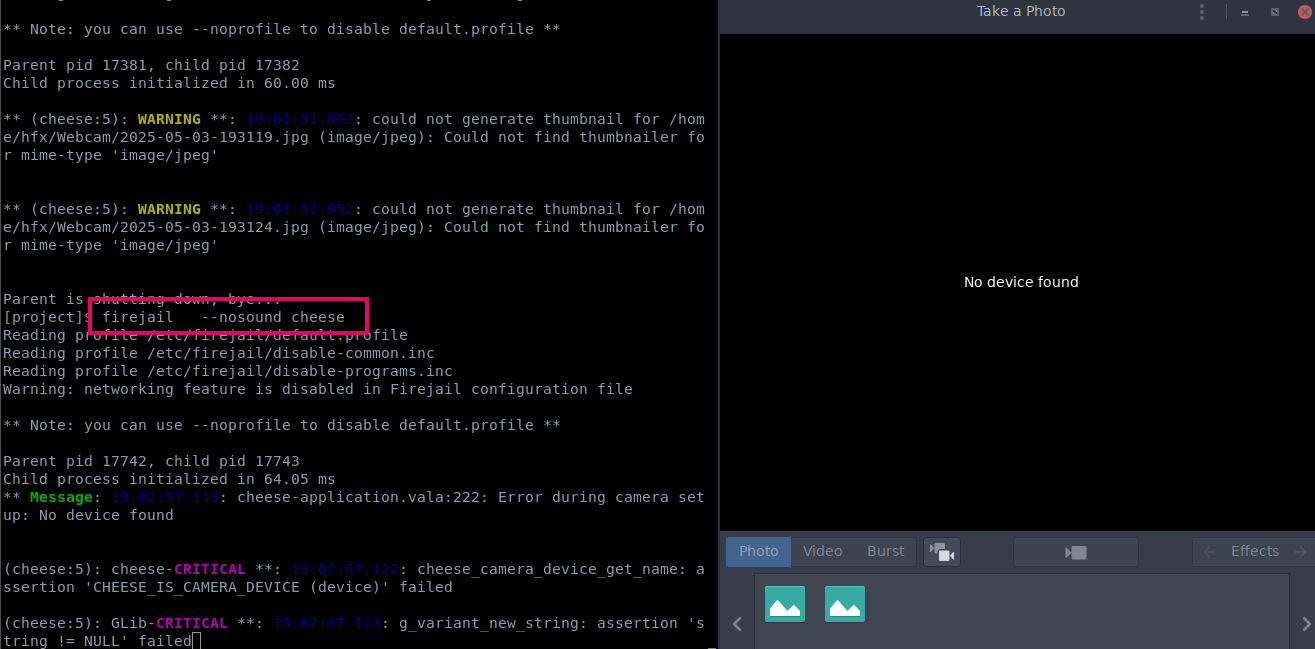
Block device access: It is unusual to provide Webcam access to every application. Block webcam access and sound with this command:
firejail --nosound cheese
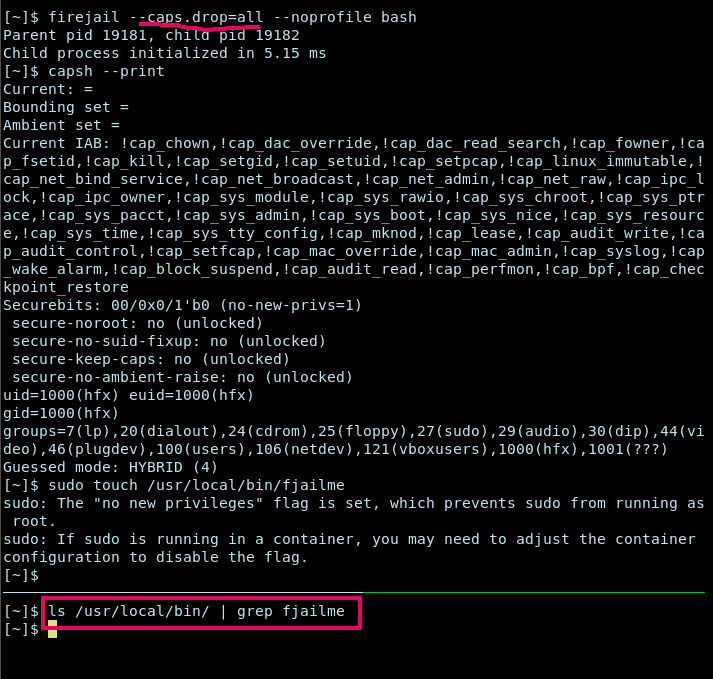
Drop All capabilities: Dropping All Capabilities means the application will have a very limited set of privileges, even if run as root, which enhances security.
firejail --caps.drop=all bash
For example, we tried to create a file in /usr/local/bin with sudo, but it didn’t work out.
Launch Appimage: With firejail, you can run AppImage in isolation.
firejail --appimage $(which Inkscape.AppImage) firejail --appimage Inkscape.AppImage # This won’t work
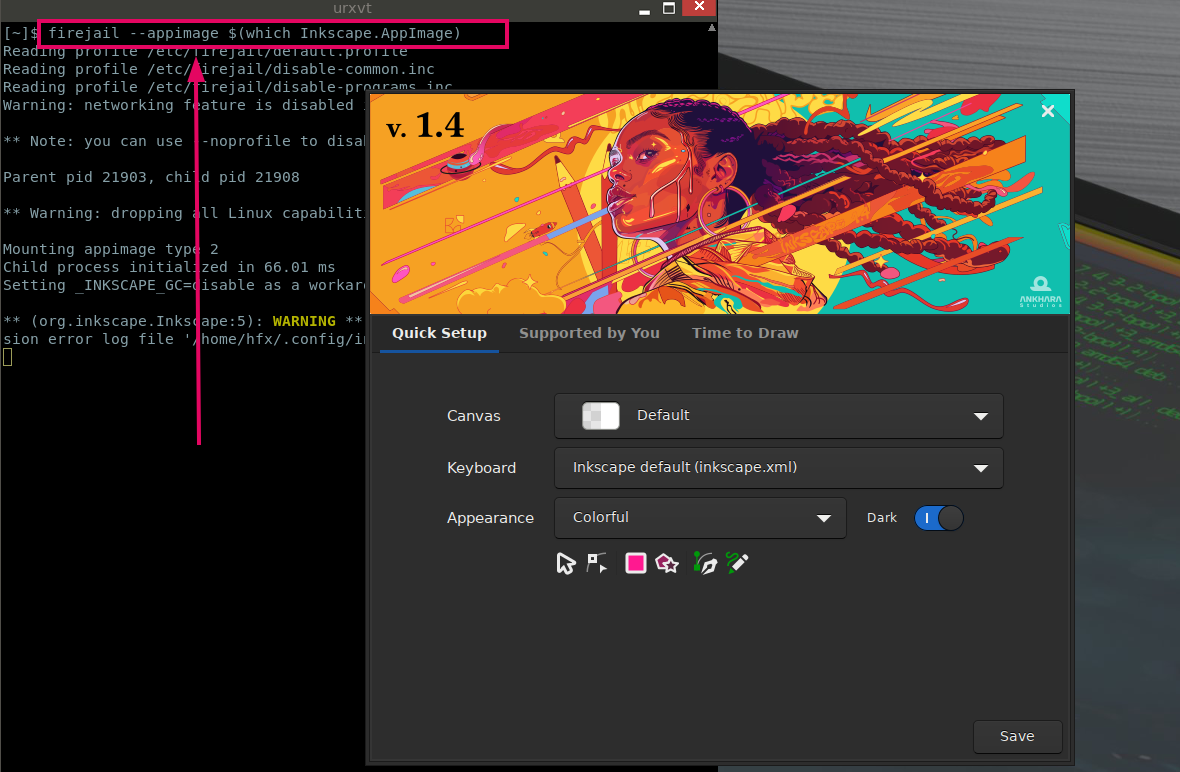
A quick note, if you have added AppImage to PATH, you won’t be able to launch it directly with firejail. You need to provide an absolute or relative path to AppImage in order to run with firejail.
Launch application in read-only mode: Aside from a security perspective, this small hack can enhance your day-to-day productivity. For example, we often use LibreOffice to open invoices, reports, or shared documents, but we rarely need to edit them. Utilizing firejail, we can open documents with LibreOffice only for viewing.
firejail --noprofile --read-only=/ --read-only=~/Documents --appimage $(which LibreOffice)
–noprofile flag skips loading the default application profile.
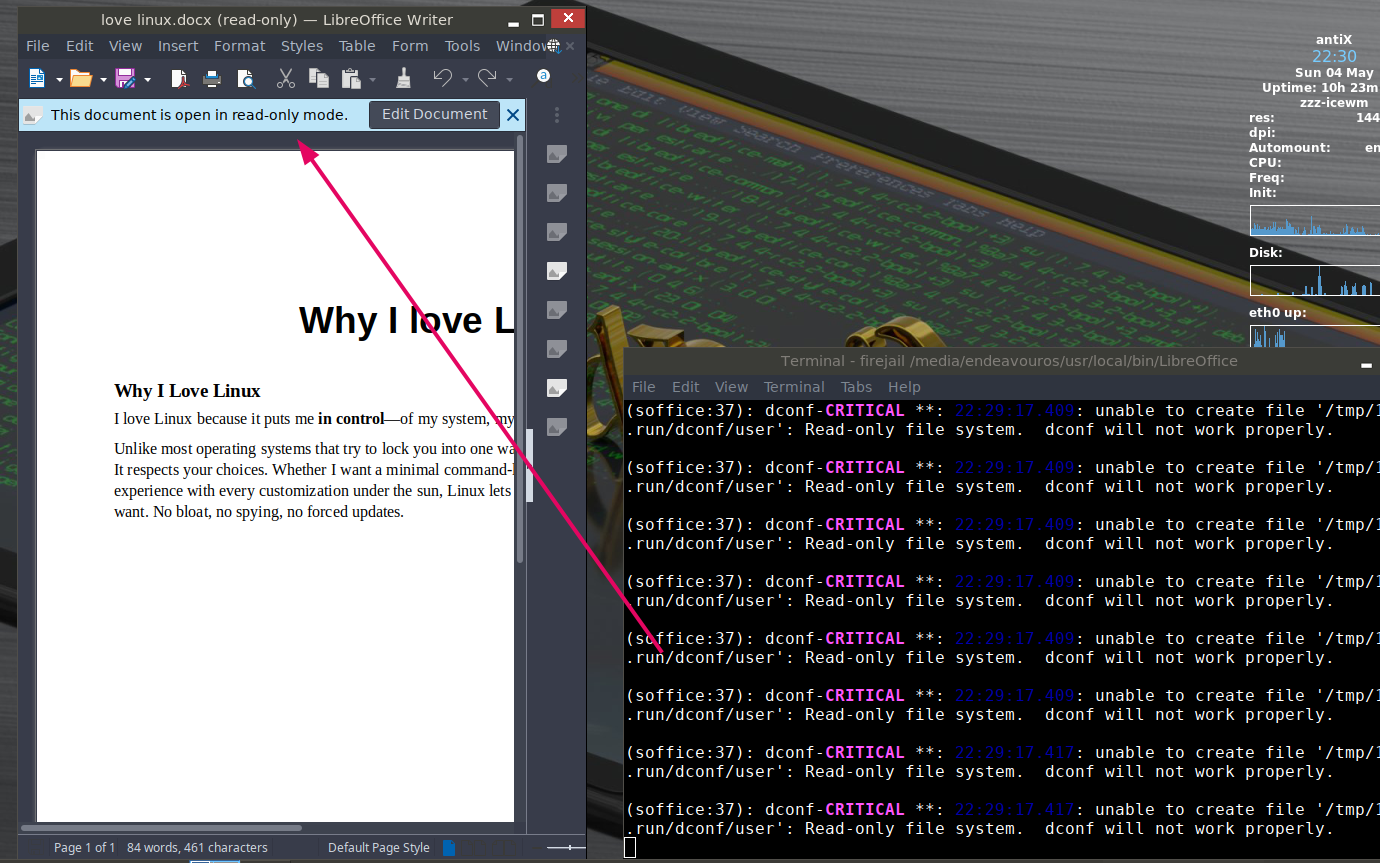
A quick note, you need to pass –readonly=/ to let LibreOffice discover Java path. Also, LibreOffice doesn’t let you open a .odt file in this mode. It might be because LibreOffice does some write operations to the odt file first.
Sandbox Linux Apps with Bubblewrap
Bubblewrap (bwrap) is a low-level Linux sandboxing tool that creates a new isolated environment for running untrusted programs. It’s installation on Debian based Linux distribution is simple, run the following command.
sudo apt install bubblewrap -y
Upon successful installation, it would provide us a bwrap CLI tool.
Key Features
- No root required (but requires unprivileged user namespace)
- Can define exactly what an application can view (filesystems, mounts, devices)
Isolate the environment using bwrap
Utilizing bubble wrap, you can first create a restrictive bash environment and then launch untrusted applications from the sandbox. The other way around is to launch a separate sandbox per application.
bwrap \ --ro-bind /usr /usr \ --ro-bind /bin /bin \ --ro-bind /lib /lib \ --ro-bind /lib64 /lib64 \ --dev /dev \ --proc /proc \ --unshare-net \ bash
Now, let’s verify how secure the sandbox is.
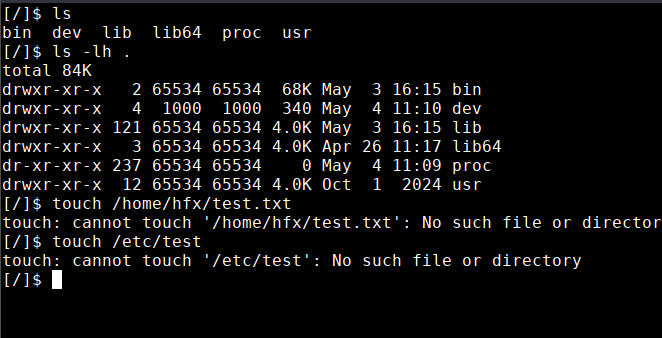
Try creating a file:
The sandbox has access to only a specific part of the file system. There’s no /home/, /etc/, /opt/ so you can be confident that launching a vulnerable application in the sandbox won’t be able to steal important files stored in the /home/<your-user> directory.
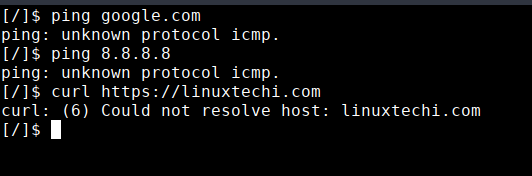
Check network connectivity:
The sandbox fails to ping any server on the internet.
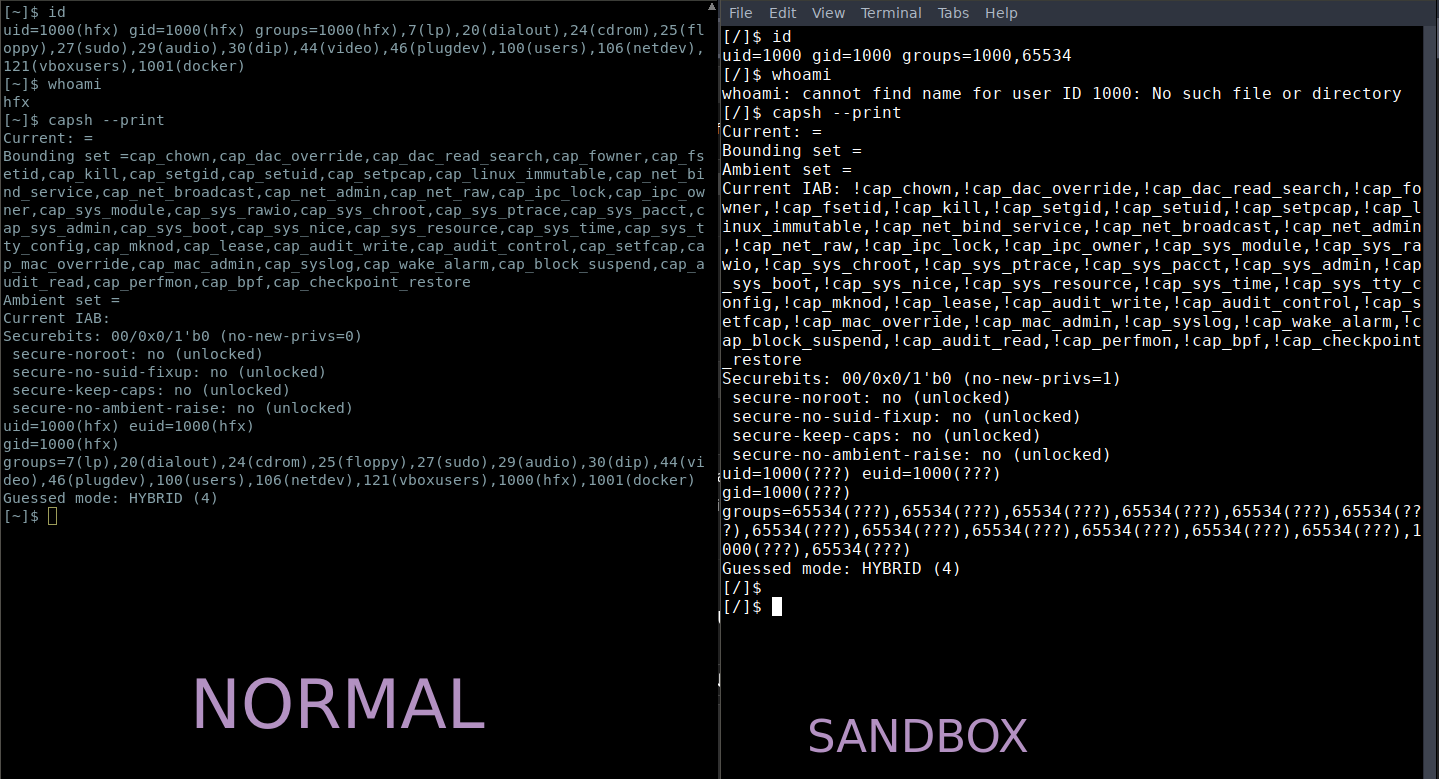
Check User and capabilities:
Try running commands such as whoami, id to verify the user identity inside the sandbox. You can also check all the capabilities with capsh. Many capabilities have been stripped off.
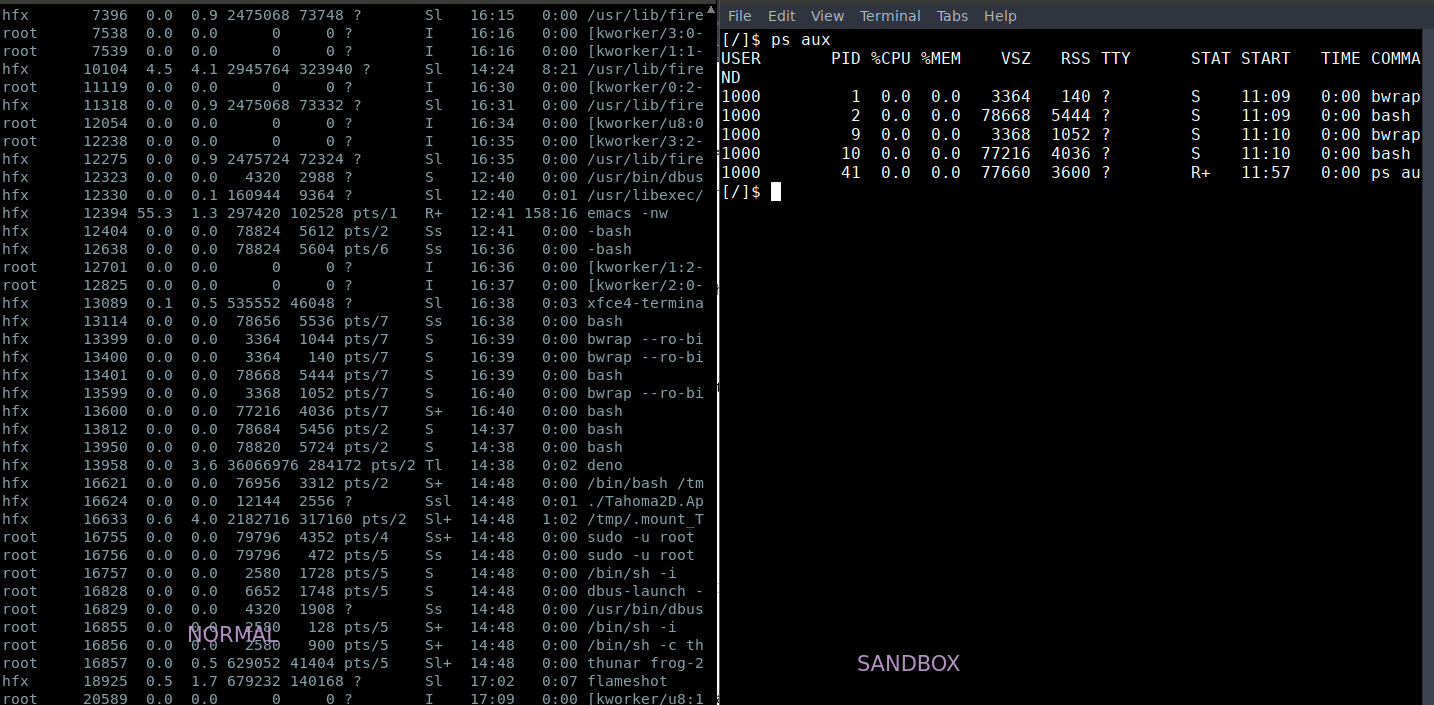
Check running processes:
bwrap hides all the running processes outside the sandbox.
FireJail vs Bubblewrap – which to choose?
On Linux systems, Bubblewrap and Firejail are two common sandboxing tools used if you need to provide an isolated environment for your applications. Their design goals and application scenarios are significantly different.
Bubblewrap is more oriented towards low-level control and is suitable for users who need a finer-grained isolation environment. It does not come with ready-made configuration templates.
Bubblewrap offers a high degree of flexibility and minimal dependencies for developers who want to precisely control their runtime environment through scripting.
Firejail, by contrast, is more focused on ease of use and is particularly well suited to desktop users. It comes with a large number of configuration files for popular programs such as Firefox, VLC, etc., which can be run in a restricted environment with a single command. Firejail offers a simple, plug-and-play solution for the average user who doesn’t want to dive into the details of the kernel but still wants to improve the security of their system.
Overall, if you’re looking to manually build a minimal sandboxed environment with clear control over the isolation logic at every step, then Bubblewrap is the better choice. If you’re concerned with fast isolation, enhanced security, and ease of use for your desktop application, then Firejail is the more hassle-free tool.
Also Read: How to Add Comments in Shell Scripts with Examples